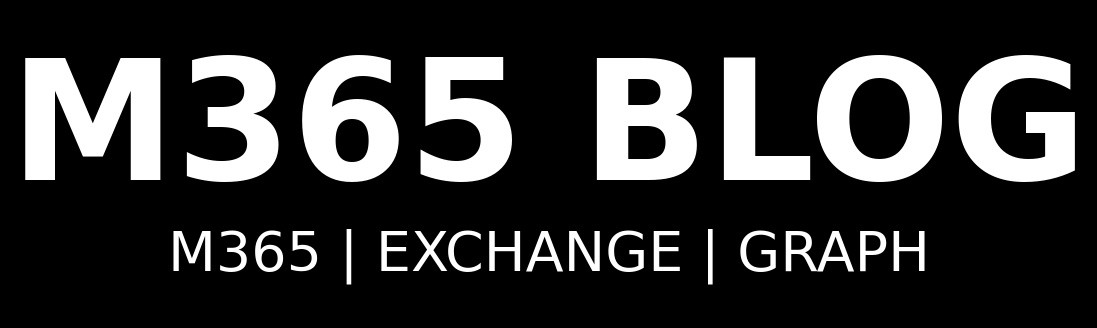Microsoft is shifting more and more towards granular access control—and with that comes the need to create a custom role in Microsoft 365. While built-in roles still serve a purpose, they often lack the precision required in modern enterprise environments. That’s where custom roles step in, especially when combined with Microsoft Entra ID and the […]
Secure Your Microsoft Graph API Access: Why and How I Implement RBAC for Applications in Exchange Online
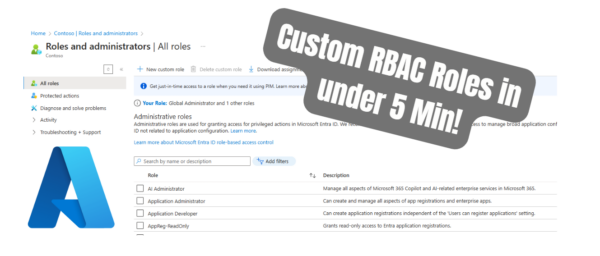
Exchange Online is continually evolving, providing more granular security controls. One crucial area I often find overlooked is securing Microsoft Graph API permissions like Mail.Send or Mail.Read. By default, applications registered in Microsoft Entra ID might have access to every mailbox within an organization. This poses significant security and compliance risks. Implementing RBAC in Exchange […]
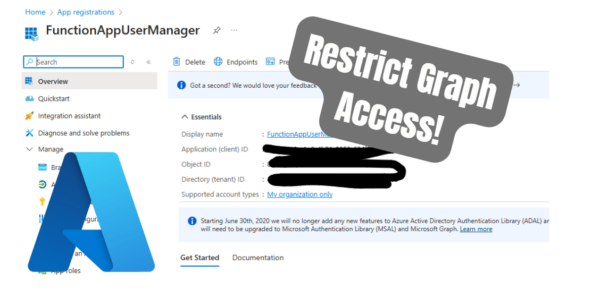
Automate Microsoft Entra User Management with Azure Function: Deactivate Inactive Users
Introduction Managing user accounts manually in Microsoft Entra can quickly become tedious and error-prone, especially when it comes to disabling inactive users. Thankfully, you can easily automate this task by creating an Azure Function to Deactivate Inactive Users. This guide provides a beginner-friendly, step-by-step approach to automating user management in Microsoft Entra using Azure Functions […]
Passkeys in Entra ID: The Future of Passwordless Authentication
Introduction Passwords are insecure, difficult to manage, and often the weakest link in IT security. Microsoft is pushing forward with passwordless authentication using Passkeys in Entra ID. But what exactly are Passkeys, and how do they differ from traditional FIDO2 keys or the Microsoft Authenticator? In this article, we explore the benefits, drawbacks, and practical […]
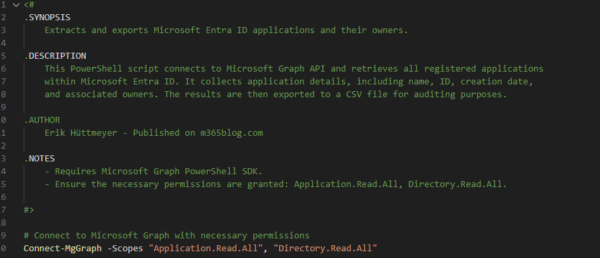
Microsoft Entra ID Audit with PowerShell and Microsoft Graph: Detect Orphaned Apps & Secure Your Cloud
Introduction Organizations increasingly rely on Microsoft Entra ID to manage authentication and access for their cloud-based applications. However, over time, some applications become orphaned—no longer actively managed or monitored—posing potential security risks. To maintain security and compliance, IT administrators must routinely perform a Microsoft Entra ID audit with PowerShell, ensuring ownership is clearly assigned. This […]
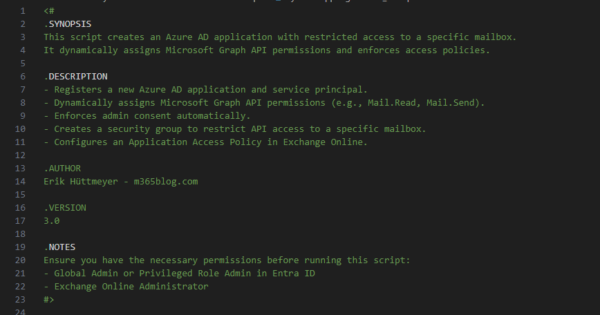
Secure Mailbox Access with Microsoft Graph & Entra ID | 🚀 The Ultimate Guide
Introduction Managing mailbox access securely in a Microsoft 365 environment can be challenging, especially when dealing with automation and API-based access. This is where my PowerShell script comes in: a robust, secure, and dynamically adaptable way to provision an Entra ID application with granular access control to a single mailbox using Microsoft Graph and Exchange […]
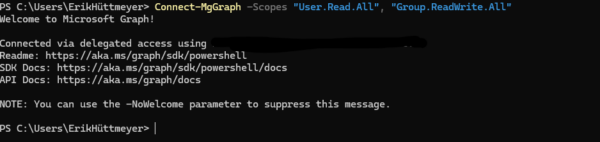
Set Up Microsoft Graph Powershell | Best Practice Implementation
How to Set Up Microsoft Graph PowerShell Microsoft Graph PowerShell is a must-have tool for IT admins and Microsoft 365 enthusiasts who want to automate tasks and manage cloud resources efficiently. In this guide, we’ll go through the setup process step-by-step and tackle common issues you might encounter. Prerequisites Before we dive in, make sure […]
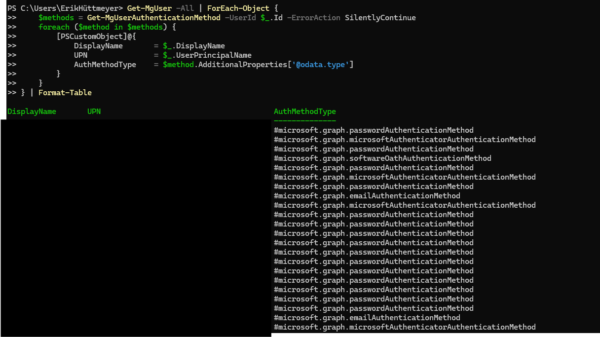
Retrieve User Authentication Methods via Microsoft Graph PowerShell
Security is a crucial topic in any Microsoft 365 environment. As IT admins, one of our key responsibilities is ensuring that users have the right authentication methods configured, especially for Multi-Factor Authentication (MFA) and passwordless sign-in. In this post, I’ll show you how to efficiently retrieve authentication methods for all users in your tenant using […]