Introduction
Managing mailbox access securely in a Microsoft 365 environment can be challenging, especially when dealing with automation and API-based access. This is where my PowerShell script comes in: a robust, secure, and dynamically adaptable way to provision an Entra ID application with granular access control to a single mailbox using Microsoft Graph and Exchange Online.
In this deep dive, I will explore how my script:
- Automates Entra ID app registration
- Dynamically assigns Microsoft Graph API permissions
- Implements an Application Access Policy for security
- Enhances manageability while maintaining security
Additionally, I will address the script’s limitations and potential future improvements. So lets Start with Secure Mailbox Access with Microsoft Graph!
Why This Script is a Game-Changer
Traditionally, granting API-based access to a mailbox required a broad set of permissions that could expose security vulnerabilities. This script mitigates those risks by leveraging Microsoft Graph API and Application Access Policies, ensuring that only the intended mailbox is accessible.
Key Benefits:
- Dynamically Configurable: Automatically retrieves and assigns the correct Microsoft Graph permissions based on defined API scopes.
- Highly Secure: Uses Exchange Online’s Application Access Policies to restrict access to a specific mailbox, reducing unnecessary exposure.
- Scalable & Maintainable: Eliminates manual Entra ID configurations, reducing administrative overhead.
- Admin Consent Automation: Automatically assigns the required permissions without needing manual intervention.
Let me break down how each component works.
Step-by-Step Breakdown
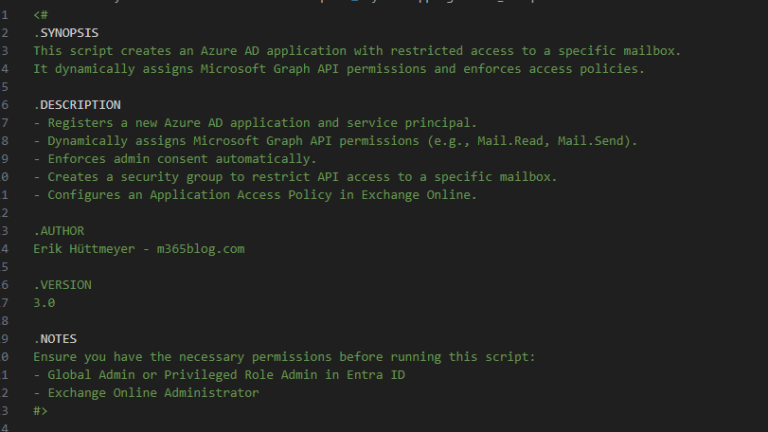
1. Registering the Entra ID Application
The first step is to create an Entra ID application that will act as the service identity for API requests. This is achieved using the following PowerShell command:
$app = New-MgApplication -DisplayName $AppName -RequiredResourceAccess $requiredResourceAccessThis automatically registers an app and associates the necessary Microsoft Graph API permissions.
2. Creating a Service Principal
Once the app is created, I need to create a Service Principal, which represents the app’s identity within Entra ID:
$sp = New-MgServicePrincipal -AppId $AppIdWithout this, the application cannot authenticate against Microsoft 365 services.
3. Granting API Permissions Dynamically
One of the script’s highlights is its ability to dynamically fetch and assign API permissions based on a predefined list:
$API_Permissions = @("Mail.Read", "Mail.Send")
$requiredResourceAccess = @(New-GraphPermissionObject -Permissions $API_Permissions)Instead of hardcoding permission GUIDs, it retrieves the correct AppRole IDs dynamically, making it adaptable to permission updates in Microsoft Graph.
4. Enforcing Admin Consent Automatically
The script also automates admin consent using the following command:
Invoke-MgGraphRequest -Method POST -Uri "https://graph.microsoft.com/v1.0/servicePrincipals/$ServicePrincipalObjectId/appRoleAssignments" -Body $Body -ContentType "application/json"This prevents the need for manual approval in the Entra Admin Center.
5. Retrieving and Decrypting the Client Secret
After creating the application, the script securely stores the Client Secret in a file. However, in scenarios where you need to retrieve and use the secret, you can decrypt it using:
$EncryptedSecret = Get-Content "C:\Temp\ClientSecret.txt" | ConvertTo-SecureString
$ClientSecret = [System.Runtime.InteropServices.Marshal]::PtrToStringAuto([System.Runtime.InteropServices.Marshal]::SecureStringToBSTR($EncryptedSecret))
Write-Host "Decrypted Client Secret: $ClientSecret"This allows you to securely insert the secret into third-party applications while maintaining security best practices.
6. Restricting API Access to a Specific Mailbox
To prevent unauthorized access, the script utilizes Exchange Online’s Application Access Policies. This ensures that the Entra ID app can only access a designated mailbox:
New-ApplicationAccessPolicy -AppId $AppId -PolicyScopeGroupId $AccessGroupName -AccessRight RestrictAccess -Description "Restricts API access to $Mailbox"This is one of the most secure ways to grant API-based access without exposing unnecessary mailboxes.
Future Plans: Certificate-Based Authentication & Cleanup Script
While Client Secrets are effective, Certificate-Based Authentication (CBA) provides several advantages, including:
- Higher Security: Certificates are harder to compromise than plaintext secrets.
- Longer Expiry Periods: Certificates typically have a longer lifecycle than Client Secrets, reducing administrative overhead.
- Improved Compliance: Organizations following strict security guidelines prefer certificate-based authentication over secret-based authentication.
I plan to explore CBA in future iterations of this script, allowing a transition to a more secure authentication method. Stay tuned for upcoming blog posts diving deeper into Certificate-Based Authentication with Entra ID and Microsoft Graph.
Additionally, I am working on a cleanup script that will completely remove an application if it was created using my method. This will ensure that any test or unused applications can be removed cleanly, including all associated permissions, policies, and service principals.
Current Limitations & Future Improvements
1. App-Only Permissions Restriction
Currently, the script only supports App-Only Permissions. It does not handle Delegated Permissions, which might be necessary in user-context scenarios.
2. Dependency on Two PowerShell Modules
The script requires both Microsoft Graph PowerShell and Exchange Online PowerShell:
Connect-MgGraph
Connect-ExchangeOnlineThis is due to the fact that Exchange Online still does not support all administrative operations via Microsoft Graph. Hopefully, Microsoft will integrate more Exchange Admin API functionalities into Graph in the future
.
3. Lack of Automated Token Retrieval
The script currently does not retrieve access tokens dynamically for API requests. While this is not an issue in an admin execution context, automation scenarios might require token management improvements.
Conclusion
This script significantly simplifies and secures the process of granting API access to a specific mailbox in Microsoft 365. By dynamically assigning permissions and enforcing Application Access Policies, it ensures that only the necessary permissions are granted, reducing security risks.
While there are some limitations, the script is highly customizable and can be extended to support more permissions, delegated access, and token management in future iterations.
For further reading, check out Microsoft’s official documentation:
If you’re managing mailbox API access in Microsoft 365, this script is a must-have in your toolkit!
Find the complete script and more resources on GitHub: M365 Blog Repository.
Keep on track and follow my Blog for more Updates!