Security is a crucial topic in any Microsoft 365 environment. As IT admins, one of our key responsibilities is ensuring that users have the right authentication methods configured, especially for Multi-Factor Authentication (MFA) and passwordless sign-in.
In this post, I’ll show you how to efficiently retrieve authentication methods for all users in your tenant using Microsoft Graph PowerShell.
🔹 Why Monitor Authentication Methods?
Understanding which authentication methods are being used helps with:
✅ Enforcing MFA adoption across your organization
✅ Identifying legacy authentication risks
✅ Monitoring passwordless adoption trends
✅ Ensuring compliance with security policies
By using Microsoft Graph PowerShell, we can retrieve this data quickly and efficiently.
🔹 Prerequisites
Before running the script, ensure you have:
📌 Microsoft Graph PowerShell SDK installed
If you haven’t installed it yet, run:
Install-Module Microsoft.Graph -Scope CurrentUser📌 Permissions:
You need the AuthenticationMethod.Read.All permission. Run this to sign in with the required scope:
Connect-MgGraph -Scopes "AuthenticationMethod.Read.All"🔹 The PowerShell Script
This script retrieves authentication methods for all users in the tenant and displays them in a structured format:
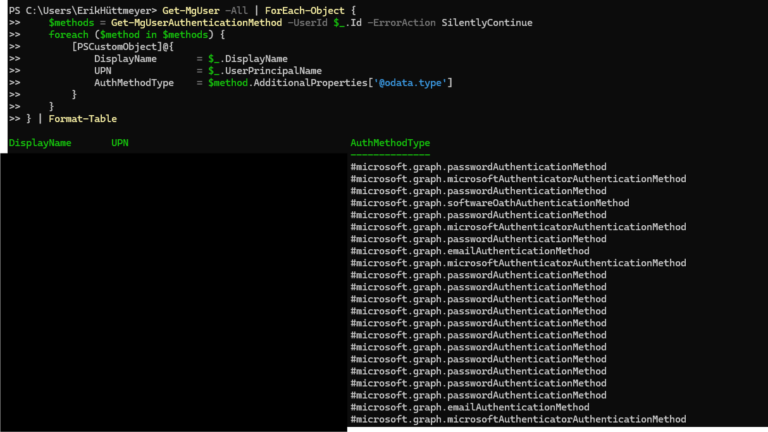
Get-MgUser -All | ForEach-Object {
$methods = Get-MgUserAuthenticationMethod -UserId $_.Id -ErrorAction SilentlyContinue
foreach ($method in $methods) {
[PSCustomObject]@{
DisplayName = $_.DisplayName
UPN = $_.UserPrincipalName
AuthMethodType = $method.AdditionalProperties['@odata.type']
}
}
} | Format-Table🔹 Explanation of the Script
1️⃣ Retrieves all users in the tenant using Get-MgUser -All.
2️⃣ Iterates over each user and fetches their authentication methods with Get-MgUserAuthenticationMethod -UserId $_.Id.
3️⃣ Parses the results to extract the @odata.type, which represents the authentication method type.
4️⃣ Outputs the data in a structured table format.
This will return details such as:
🔹 User Display Name
🔹 User Principal Name (UPN)
🔹 Authentication Method Type (e.g., microsoftAuthenticator, email, phone)
🔹 Example Output
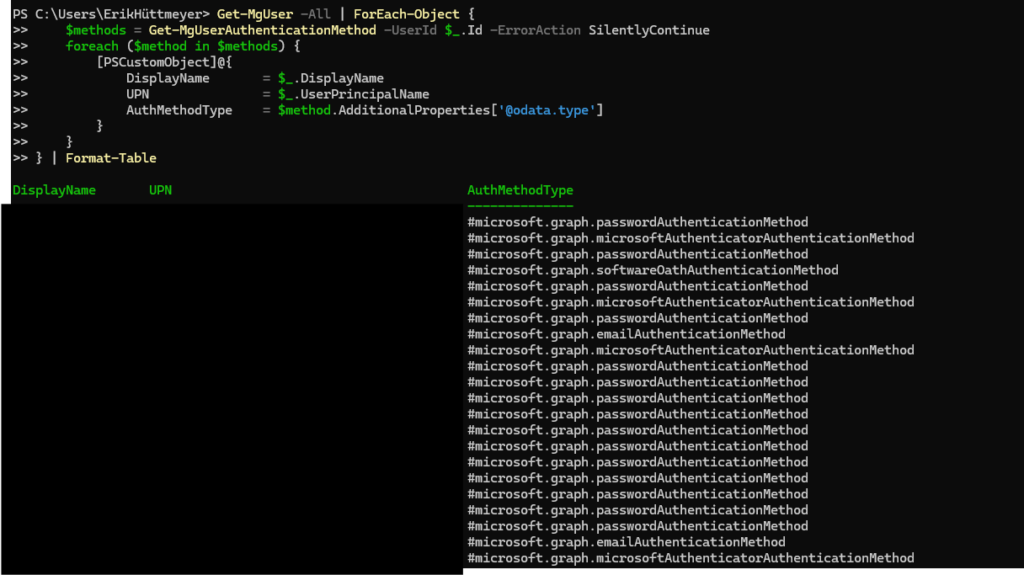
This gives you a clear overview of the authentication landscape in your tenant.
🔹 Final Thoughts
This script is a great way to audit authentication methods and ensure security compliance in your Microsoft 365 environment. By leveraging Microsoft Graph PowerShell, you get an elegant, scalable, and modern approach compared to legacy PowerShell modules.
🔹 Next Steps:
✔️ Run the script in your environment
✔️ Identify users missing MFA or using weak authentication methods
✔️ Use the exported CSV for further security analysis
🚀 Stay tuned for more Graph to Know posts, where I simplify Microsoft Graph API for IT professionals!
💬 What’s Next?
Do you have any specific use cases where you need authentication insights? Let me know in the comments, and I might cover them in the next Graph to Know post! 🚀