How can you boost your Exchange Hybrid inbound mail security?
In a hybrid Exchange environment, ensuring that only authorized messages reach your on-premises Exchange servers is crucial for security. If your MX record points to Office 365, you should configure your firewall to block all inbound email traffic except from Microsoft’s public IP addresses. That way you can improve your Exchange Hybrid inbound mail security However, this alone is not sufficient, as any Microsoft 365 tenant could still send emails directly to your server. That causes a lot of Problems…
To mitigate this, we need to implement an additional mail flow rule based on the X-MS-Exchange-Organization (XORG) header.
Why Restrict Direct Inbound Email and improve Exchange Hybrid inbound mail security?
When using Exchange Hybrid, your on-premises Exchange servers should only receive emails from trusted sources, such as Exchange Online Protection (EOP). If left unrestricted, malicious actors or even other Microsoft 365 tenants could send emails directly to your on-premises servers, bypassing your organization’s intended security policies. By enforcing these restrictions, you:
- Ensure only authorized Microsoft 365 tenants can send emails to your on-premises Exchange.
- Prevent unauthorized mail delivery from other tenants using Microsoft’s infrastructure.
- Reduce attack surfaces for potential exploits.
Firewall Configuration: Blocking Non-Microsoft Traffic
Restrict inbound SMTP traffic (port 25) to only allow Microsoft 365 public IPs
- Obtain the latest Microsoft 365 IP ranges from Microsoft’s official documentation.
- Configure your firewall to allow only these IP ranges for SMTP traffic.
- Block all other external inbound SMTP traffic.
Creating an Audit Mail Flow Rule
Even after restricting inbound SMTP traffic at the firewall, your Exchange server can still receive mail from any Microsoft 365 tenant. To address this, you need to create a transport rule that inspects the X-MS-Exchange-Organization or X-OriginatorOrg (XORG) header and ensures that only emails from your own tenant are accepted.
However, before enforcing this restriction, it is best practice to set up the rule in audit mode first. This allows you to log and analyze mail flow, ensuring that no critical internal applications relaying through Exchange are unintentionally blocked.
Step-by-Step Guide to Creating the Rule in Audit Mode
- Access Exchange Admin Center (EAC)
- Navigate to the Exchange Admin Center (EAC) in your on-premises Exchange environment.
- Create a New Mail Flow Rule
- Go to Mail Flow > Rules and click on New.
- Choose Create a new rule.
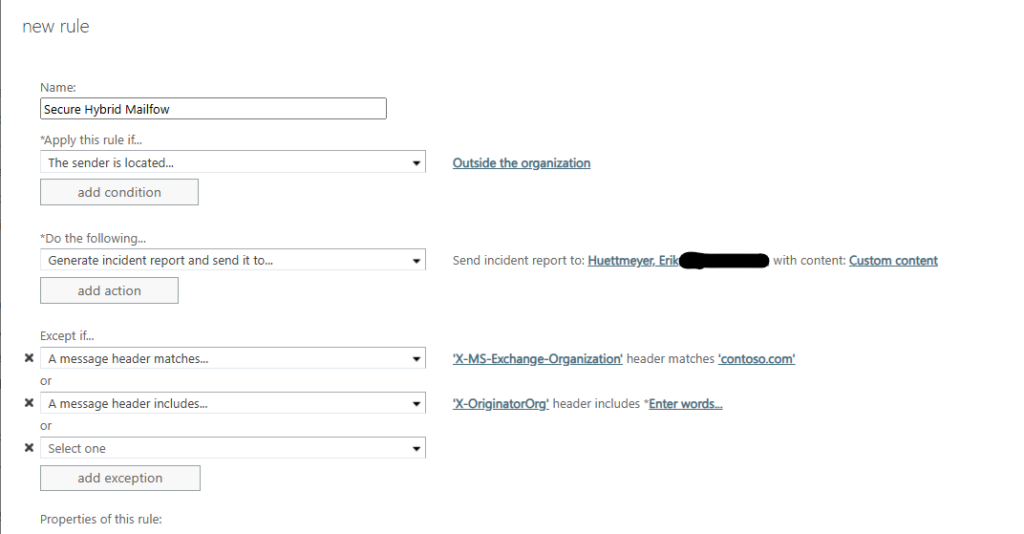
- Define the Conditions
- Name the rule: Audit Inbound Email from Unauthorized Microsoft 365 Tenants
- Apply the rule if:
- The message header
X-MS-Exchange-OrganizationorX-OriginatorOrg
- The message header
- Set the Action to Generate an Incident Report
- Instead of rejecting messages, select Generate an incident report and configure it to send alerts to the administrator.
- This ensures all messages that would have been blocked are logged for review before full enforcement.
- Save and Enable the Rule
- Review the settings and activate the rule.
Monitor Rule
After enabling the audit rule, monitor mail flow for a few weeks:
- Review logs to identify any internal applications or services that might be relaying through Exchange.
- If necessary, create exceptions for legitimate relays before enforcing the restriction.
Enforcing the Rule
Once you have verified that only unauthorized tenants are logged in the audit phase, you can switch the rule to block mode:
- Edit the existing rule.
- Change the action from Generate Incident Report to Reject the message with an explanation.
- Provide a rejection message, such as: This mail server only accepts mail from our Microsoft 365 tenant. Contact IT for assistance.
- Save and apply the updated rule.
Verifying the Configuration
Since testing direct SMTP delivery is complex, check the message headers in received emails by examining the X-MS-Exchange-Organization field to confirm that unauthorized messages are being rejected.
Security Considerations for Hybrid Configuration Wizard (HCW)
The Hybrid Configuration Wizard (HCW) simplifies hybrid deployments but also introduces security considerations:
- Restrict Hybrid Management Access: Limit access to hybrid management to.
- Monitor Hybrid Connectivity: Regularly audit and monitor hybrid connectors to detect any anomalies.
- Apply Security Updates: Keep your Exchange servers up to date to mitigate potential vulnerabilities.
Conclusion
Restricting inbound email to only allow messages from authorized Microsoft 365 tenants is a crucial step in securing your hybrid Exchange environment. By implementing a firewall rule to block non-Microsoft traffic and an Exchange transport rule to enforce tenant-level restrictions, you ensure that your mail flow remains secure. Setting the rule to audit mode first helps identify any internal applications relying on Exchange before enforcement.
By following these best practices, you enhance the security posture of your Exchange environment and minimize risks associated with email threats.
For more Information, Guides and News follow my Blog!