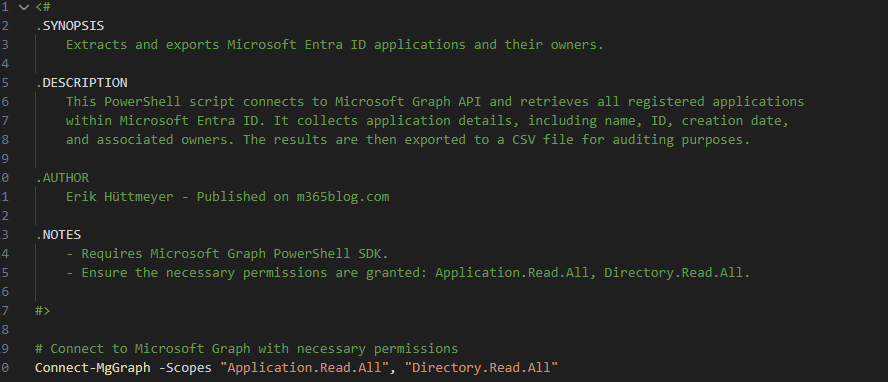
Introduction
Organizations increasingly rely on Microsoft Entra ID to manage authentication and access for their cloud-based applications. However, over time, some applications become orphaned—no longer actively managed or monitored—posing potential security risks.
To maintain security and compliance, IT administrators must routinely perform a Microsoft Entra ID audit with PowerShell, ensuring ownership is clearly assigned. This guide walks through a PowerShell-based approach to retrieve all applications within Microsoft Entra ID, analyze ownership details, and export the data to a CSV file for further review.
Why Regularly Auditing Entra ID Applications is Important
Neglected applications can introduce vulnerabilities:
- Security Risks: Orphaned applications can be exploited by attackers due to lack of monitoring.
- Compliance Violations: Organizations often require active ownership tracking for applications to meet regulatory standards.
- Operational Inefficiencies: Unused applications consume resources and complicate system administration.
By using this automated PowerShell script, IT teams can efficiently identify orphaned applications, remove redundant entries, and improve overall security.
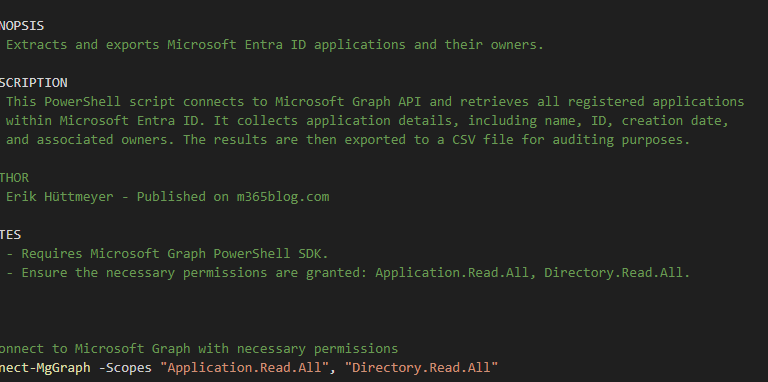
How the PowerShell Script Works
The script, available on GitHub, interacts with Microsoft Graph API to extract a list of all registered applications, retrieve ownership data, and generate a structured CSV report. So you can get a quick Microsoft Entra ID audit with PowerShell and Microsoft Graph
Prerequisites
Before executing the script, ensure the following:
- PowerShell is installed on your system.
- The Microsoft Graph PowerShell SDK is installed.
- The necessary permissions are granted:
Application.Read.AllandDirectory.Read.All.
For installation assistance, refer to this guide.
Connecting to Microsoft Graph
To authenticate and retrieve application data, run:
Connect-MgGraph -Scopes "Application.Read.All", "Directory.Read.All"This ensures that PowerShell has the required access to query Entra ID applications.
Retrieving Applications
The script leverages the Get-AllMgApplications function to collect application data:
function Get-AllMgApplications {
$uri = "https://graph.microsoft.com/v1.0/applications"
$applications = @()
do {
$response = Invoke-MgGraphRequest -Uri $uri -Method GET
$applications += $response.value
$uri = $response.'@odata.nextLink'
} while ($uri)
return $applications
}This function:
- Queries Microsoft Graph API for all registered applications.
- Handles pagination to ensure all applications are retrieved.
- Returns a complete dataset for further processing.
Extracting Application Ownership Information
To determine ownership, the script runs:
$owners = Get-MgApplicationOwner -ApplicationId $app.idExporting Data to CSV
After gathering all relevant data, the script formats and exports the results:
$csvPath = "$PSScriptRoot\Entra_Applications.csv"
$results | Export-Csv -Path $csvPath -NoTypeInformation -Encoding UTF8This CSV file provides an easy-to-read report that can be analyzed in Excel or other data-processing tools.
Use Cases and Benefits
- Identify Orphaned Applications: Pinpoint applications lacking assigned owners and take action.
- Enhance Security Posture: Reduce the attack surface by decommissioning unnecessary applications.
- Support Compliance Efforts: Ensure application ownership aligns with regulatory and security requirements.
- Improve IT Visibility: Maintain an up-to-date inventory of applications and their responsible parties.
Final Thoughts and Next Steps
Unmonitored applications in Microsoft Entra ID create unnecessary risk. Regular audits help prevent unauthorized access and reduce security threats.
Using this PowerShell-based audit tool, IT administrators can efficiently analyze their Entra ID environment, secure unmanaged applications, and ensure proper governance.
What to do?
- Download the script from GitHub.
- Run an audit to detect and resolve orphaned applications.
- Strengthen security policies by enforcing ownership rules.
- By implementing this proactive approach, organizations can mitigate security risks and improve operational efficiency. 🚀